enable
conf t
hostname abc
banner motd ? Unauthorized access is not ok ?
no IP domain-lookup
ip domain-name abc.com
crypto key generate rsa (use 2048)
ip ssh version 2
enable secret abc
username admin secret 12345
(if use command “username admin privilege 15 secret 12345″, the user admin has the “enable” access right way once login to the device without typing “enable”. note: the privilege 15 is not working when using aaa new-model, aaa authentication enable default enable )
line vty 0 4
logging synchronous
login local
transport input ssh (only allow ssh connection. To enable ssh, please run hostname, ip domain-name and crypto key generate rsa first)
transport output ssh
exec-timeout 0 0 (minutes seconds, 0 means unlimited)
(note: in Cisco packet tracer, using “transport input ssh telnet” packet tracer says that telnet is invalid input. If I swap ssh and telnet, it says ssh is invalid. There must be a bug in packet tracer. “transport input ssh telnet” works on cisco switch 3750 )
line con 0
login local
logging sync
line vty 5 15
no login
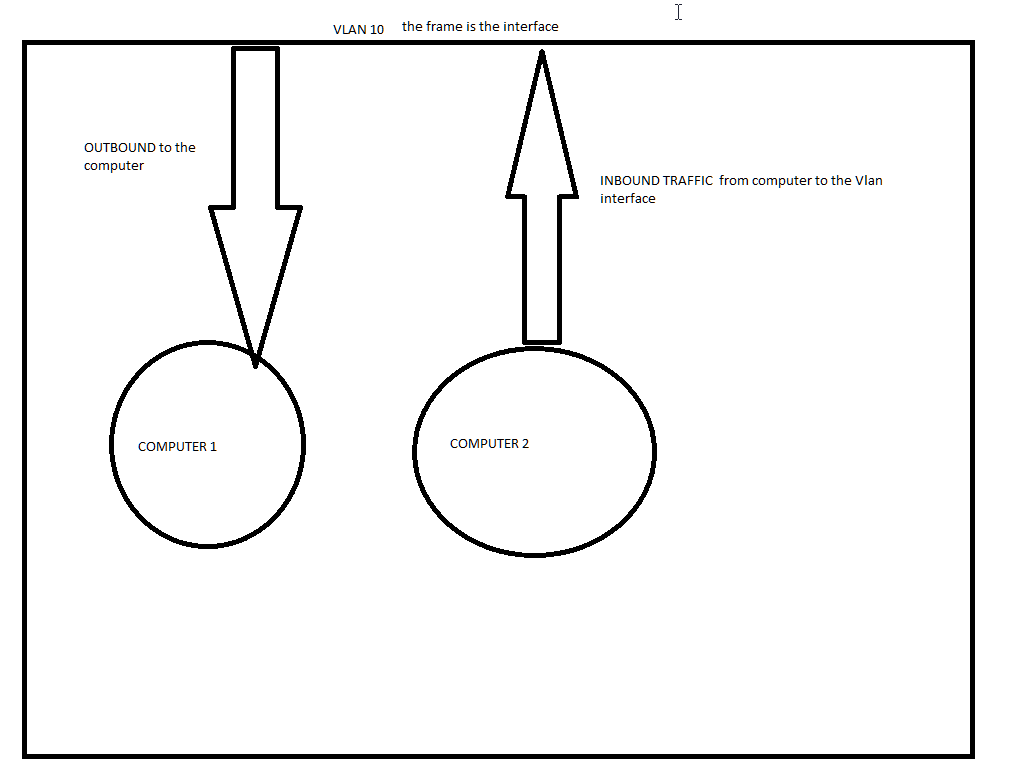
vlan 10
name server
interface vlan 10
ip address 1.1.1.1 255.255.255.0
interface vlan 1
ip address 10.10.10.10 255.255.255.0
no shutdown
int g1/0/1
switchport mode access
switchport access vlan 10
interface g1/0/23
switchport trunk encapsulation dot1q (for older switches)
switchport mode trunk
switchport nonegeotiate
int g1/0/2 (for a layer 3 switch or a router, assign a physical port ip address)
no switchport
ip address 2.2.2.2 255.255.255.0
Vtp mode transparent
Ntp server 132.246.11.227 (or use 216.239.35.4)
Clock timezone AST -4
Clock summer-time ADT recurring
No vstack
Ip default-gateway 192.168.30.111 ****** (don’t use if ip route is enabled)
* configure and verify EtherChannel (port channel)
int range g1/0/1-2
channel-group 1 mode active (using LACP mode, the connected partner switch needs to use passive. choose desirable/auto if prefer PAGP mode, which is Cisco proprietary protocol)
show etherchannel summary; show etherchannel port-channel; show interfaces port-channel 1(show etherchannel status)
service password-encryption (optional, if not using secret for enable password and use line vty password)
 .
.